Warden allows you to set stronger Postfix restrictions so that the bulk of spam is rejected at the SMTPD level before it gets processed by Amavis (this will help with server load).
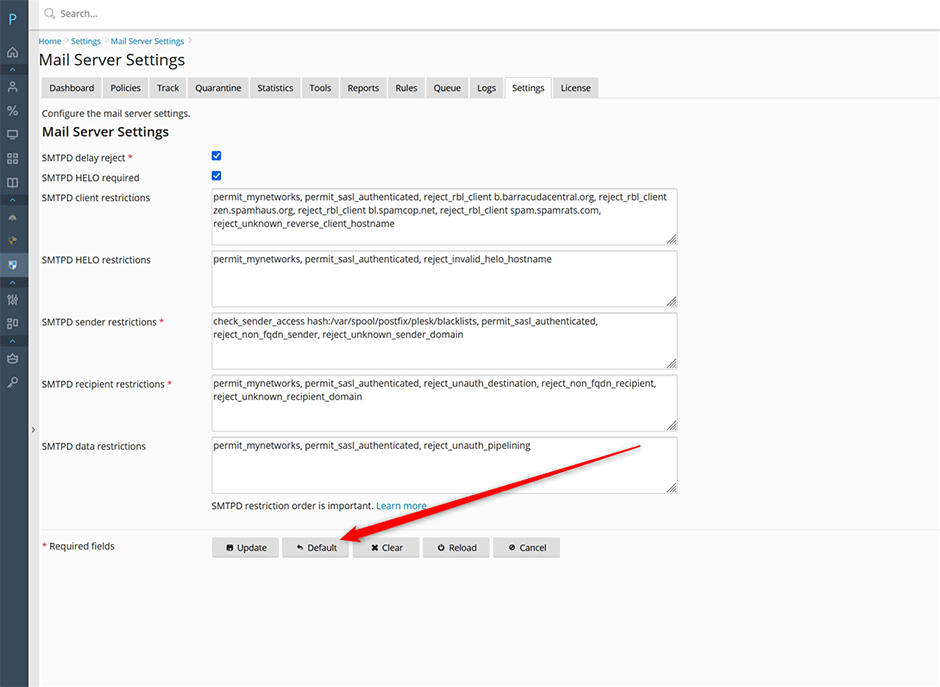
- To apply the recommended SMTPD restrictions go to Warden -> Settings -> Mail Server Settings and press the Default button.
- To remove the recommended SMTPD restrictions (only if you have trouble) go to Warden -> Settings -> Mail server Settings and press the Clear button.
- Admins can whitelist clients from these restrictions under Warden -> Settings-> Mail Server Access.
- Many of these restrictions use DNS queries to determine if the connecting client has proper DNS records that a legitimate mail server would have in place so make sure that your DNS is functioning properly before you enable these restrictions.
- The recommended restrictions should work for the majority of users as they are not strictest that can be applied and have been tested on large volume mail servers.
- Detailed information about all available restrictions can be found here.
- Detailed information about mail server access controls can be found here.
What Restrictions are Applied?
Default Restrictions (Before)
These default options are located in the postfix configuration file /etc/postfix/main.cf
smtpd_client_restrictions = permit_mynetworks, permit_sasl_authenticated
smtpd_sender_restrictions = check_sender_access hash:/var/spool/postfix/plesk/blacklists, permit_sasl_authenticated
smtpd_recipient_restrictions = permit_mynetworks, permit_sasl_authenticated, reject_unauth_destinationStronger Restrictions (After)
Note: The smtpd_client_restrictions option might have reject_rbl_client entries added if you enabled DNSBLs under Tools & Settings -> Mail Server Settings -> DNS zones for DNSBL service. Warden will just add the reject_unknown_reverse_client_hostname entry after any reject_rbl_client entries.
smtpd_delay_reject = yes
smtpd_helo_required = yes
smtpd_client_restrictions = permit_mynetworks, permit_sasl_authenticated, reject_unknown_reverse_client_hostname
smtpd_helo_restrictions = permit_mynetworks, permit_sasl_authenticated, reject_invalid_helo_hostname
smtpd_sender_restrictions = check_sender_access hash:/var/spool/postfix/plesk/blacklists, permit_sasl_authenticated, reject_unknown_sender_domain
smtpd_recipient_restrictions = permit_mynetworks, permit_sasl_authenticated, reject_unauth_destination, reject_unknown_recipient_domain
smtpd_data_restrictions = permit_mynetworks, permit_sasl_authenticated, reject_unauth_pipelining
Note: SMTPD restrictions options are processed from left to right so ordering is important. The permit_mynetworks option is an important boundry between clients on your internal network and clients outside. Options that appear before permit_mynetworks apply to both internal and external clients while those after permit_mynetworks apply to external clients only.
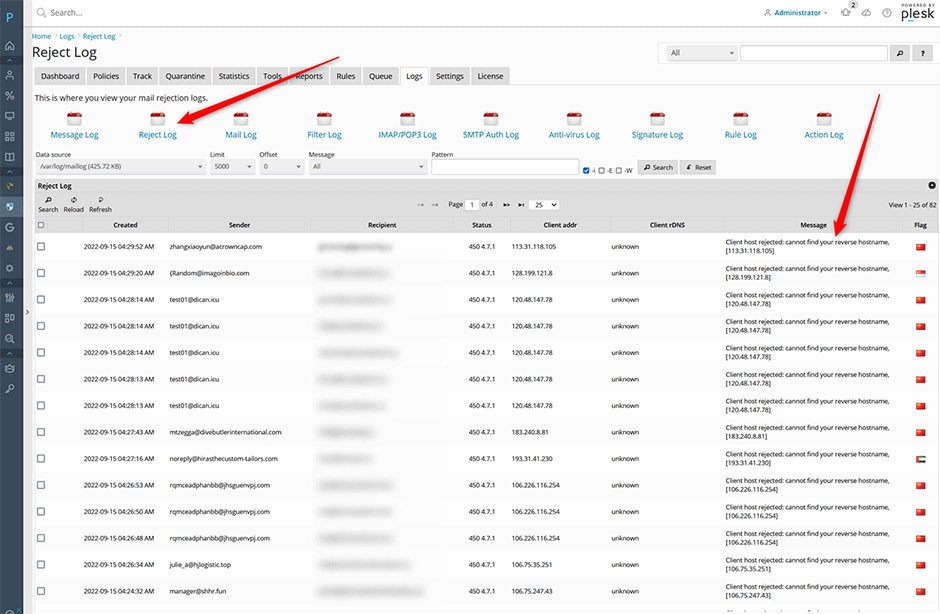
Reject Log
Mail rejected by these restrictions will be listed under Warden -> Logs -> Reject log. Admins can use the message dropdown to search for specific messages.
smtpd_client_restrictions - will be logged with the message: Client host rejected
smtpd_helo_restrictions - will be logged with the message: Helo command rejected
smtpd_sender_restrictions - will be logged with the message: Sender address rejected
smtpd_recipient_restrictions - will be logged with the message: Recipient address rejected
smtpd_data_restrictions - will be logged with the message: Data command rejected
Restrictions Explained
smtpd_delay_reject - Wait until the RCPT TO command before evaluating restrictions. This should always be enabled because some clients mis-behave when the Postfix SMTP server rejects commands before RCPT TO. It also allows Postfix to log recipient address information when rejecting a client name/address or sender address, so that it is possible to find out whose mail is being rejected.
smtpd_helo_required - Require that a remote SMTP client introduces itself with the HELO or EHLO command before sending the MAIL command or other commands that require EHLO negotiation. This is required when using smtpd_helo_restrictions otherwise clients would be able to bypass those restrictions.
smtpd_client_restrictions
reject_unknown_reverse_client_hostname - Reject the request when the client IP address has no address->name mapping. This is a weaker restriction than reject_unknown_client_hostname, which requires not only that the address->name and name->address mappings exist, but also that the two mappings reproduce the client IP address. The unknown_client_reject_code parameter specifies the response code for rejected requests (default: 450). The reply is always 450 in case the address->name or name->address lookup failed due to a temporary problem.
smtpd_helo_restrictions
reject_invalid_helo_hostname - Reject the request when the HELO or EHLO hostname is malformed. The invalid_hostname_reject_code parameter specifies the response code for rejected requests (default: 501).
smtpd_sender_restrictions
reject_unknown_sender_domain - Reject the request when Postfix is not the final destination for the sender address, and the MAIL FROM domain has 1) no DNS MX and no DNS A record or 2) a malformed MX record such as a record with a zero-length MX hostname. The reply is specified with the unknown_address_reject_code parameter (default: 450), unknown_address_tempfail_action (default: defer_if_permit), or 550 (nullmx, Postfix 3.0 and later).
smtpd_recipient_restrictions
reject_unknown_recipient_domain - Reject the request when Postfix is not final destination for the recipient domain, and the RCPT TO domain has 1) no DNS MX and no DNS A record or 2) a malformed MX record such as a record with a zero-length MX hostname. The reply is specified with the unknown_address_reject_code parameter (default: 450), unknown_address_tempfail_action (default: defer_if_permit), or 550 (nullmx, Postfix 3.0 and later).
smtpd_data_restrictions
reject_unauth_pipelining - Reject the request when the client sends SMTP commands ahead of time where it is not allowed, or when the client sends SMTP commands ahead of time without knowing that Postfix actually supports ESMTP command pipelining. This stops mail from bulk mail software that improperly uses ESMTP command pipelining in order to speed up deliveries.
Response Codes
By default most of the new restrictions respond with a 450 status code (a temporary failure in mail delivery) meaning that the connecting client may try to re-attempt delivery again. There is a debate whether administrators should change the default response from a 450 status to a stronger 550 status so that the email will be rejected instantly. You can see the pros and cons in these threads:
2. unknown_client_reject_code 450 vs. 550
Administrators can set the unknown_client_reject_code and unknown_address_reject_code under Warden -> Settings -> Mail Server Settings
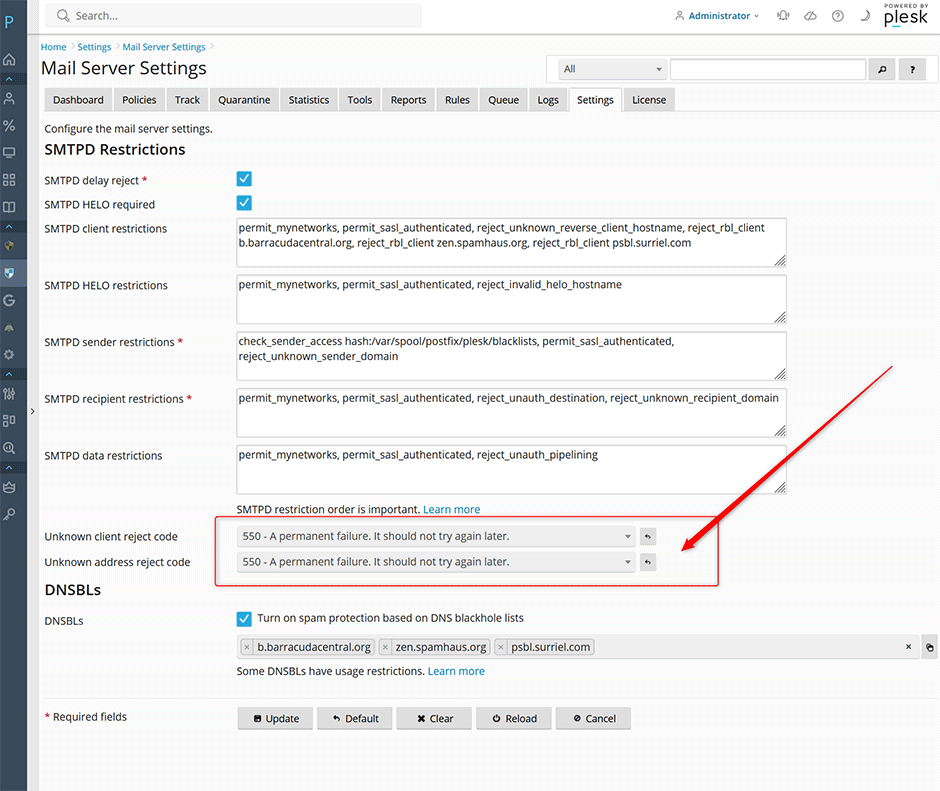
You can also change them using the CLI:
// to change the reject_unknown_reverse_client_hostname response code from 450 to 550
postconf unknown_client_reject_code=550
// to change the reject_unknown_sender_domain and reject_unknown_recipient_domain response codes from 450 to 550
postconf unknown_address_reject_code=550
// reload postfix
postfix reload
