Juggernaut Firewall supports denying IP addresses at the web server level based on their country, continent, or autonomous system number. To enable web server level geo-filtering in Juggernaut Firewall:
Get a MaxMind License Key
- The Apache mod_maxmind geolocation module requires that the Maxmind GeoIP2 databases be installed on the server. Signup for the free license key here.
- Generate a license key here (When asked - Will this key be used for geoipupdate? Choose: no)
- Navigate to Juggernaut Firewall -> Settings -> Geolocation Settings and enter the license key under MaxMind license key. (It may take up to 15 minutes before MaxMind will recognize a newly created API key).
- Press the update button to save the license key and to download the MaxMind city and ASN databases.
Enable the Apache MaxMind DB module
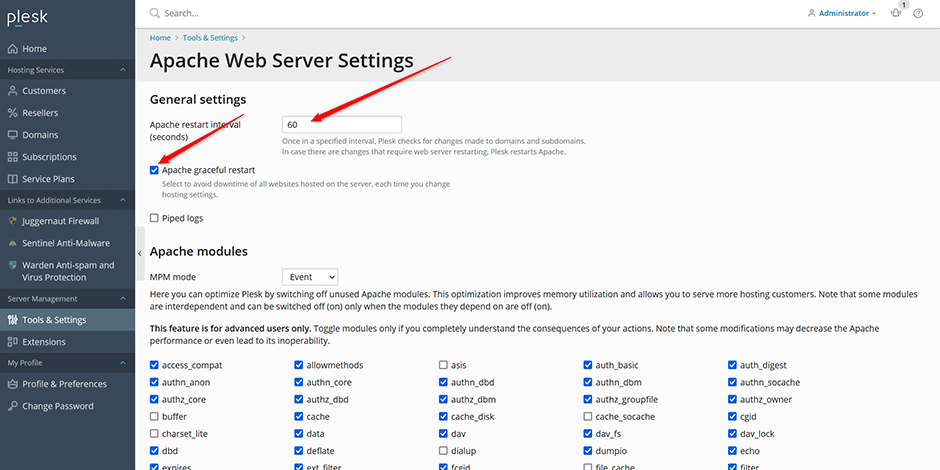
1. In Plesk navigate to Tools & Settings -> General Settings -> Apache Web Server and set the Apache restart interval (60 seconds is recommended for a server with a lot of customers). Also make sure that Apache graceful restart is enabled. This will ensure that there will be minimal Apache disruptions when the Juggernaut Firewall applies any changes to the domains configuration files.
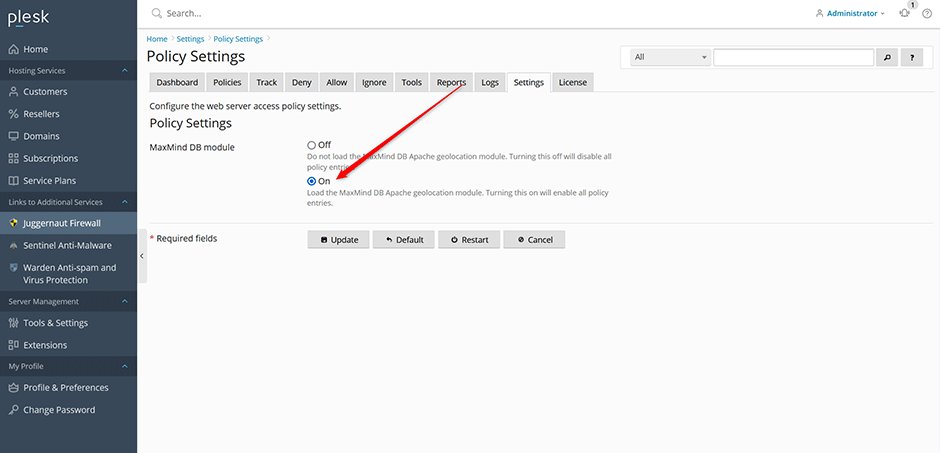
2. Navigate to Juggernaut Firewall -> Settings -> Web Server -> Policy Settings and set the MaxMind DB module radio option to "On". Press the update button apply the changes. The MaxMind databases must be downloaded before the Apache module can be enabled.
About Policies
- Server wide policies (the first domain entry labeled "server wide" in the policy grid) apply to all domains on the server and cannot be overwritten at the domain level. If you block a country server wide you cannot allow it for a single domain.
- Be careful not to block any search engines or third party APIs that your websites may use.
- Be careful when adding "allow" entries. Allow entries will only "allow" the countries, continents, or autonomous system numbers that you set. Any non-matching entities will be denied access.
- Policy management is currently disabled by default for non-admins. If you want to give access to resellers or customers then you give them permission under Juggernaut Firewall -> Settings -> Permissions. Make sure that the Apache restart interval and Apache graceful restart options are set properly in Plesk before you give non-admins permission.
- The webmail policy requires that server wide geo-filtering be enabled. If you add a webmail policy then server wide geo-filtering will be automatically enabled if it isn't already.
- Because mod_maxmind is an Apache module, the domains PHP handler must be set to use Apache otherwise geo-filtering will not work. Nginx proxy mode must also be set to proxy requests to Apache.
- Apache configurations use the "AuthMerging And" directive so that authorization logic is combined with that of the nearest predecessor. E.g. If you allow a certain country for a domain and the domain has a .htaccess requiring a username and password then BOTH options must be satisfied before access is granted.
- If a location has both a deny and allow policy then BOTH policies will have to be satisfied to allow access.
Adding a Policy
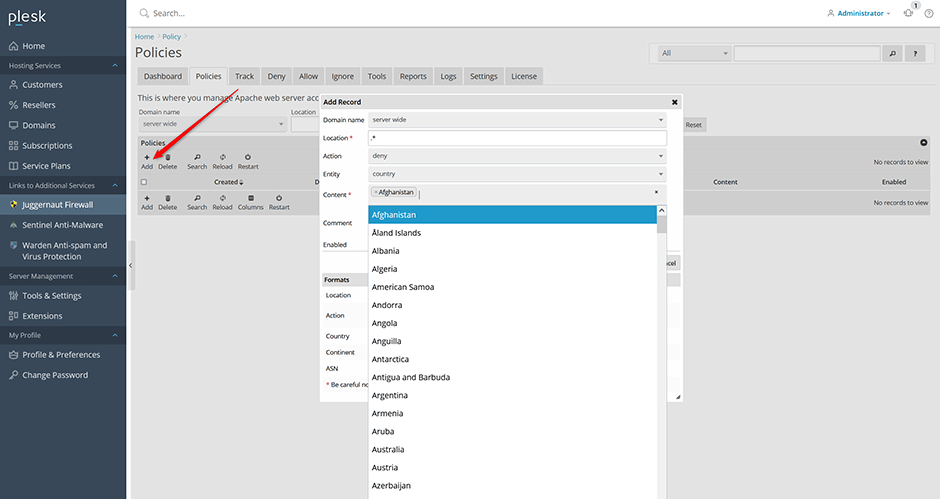
1. Navigate to Juggernaut Firewall -> Policies and click on a domain to add a policy entry. If this is the first entry for the domain then geo-filtering will be automatically enabled. The location option allows you match entire domain .* or for a single URI only. For example if we wanted to only allow certain countries to be able to login to wordpress we could set the location to /wp-login.php. If we wanted to allow certain countries access to the wordpress admin backend then we could set the location to /wp-admin/.*. The location option supports basic regex and uses the Apache LocationMatch directive internally.
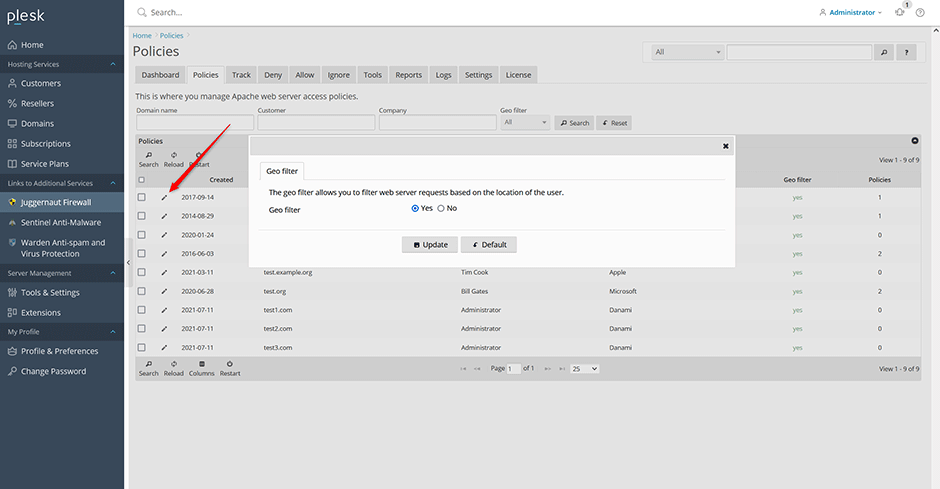
Geo-filtering can be enabled/disabled server wide or per domain by pressing the edit icon next to the server wide or the specific domain on the policies page. The geo-filter can has three options - yes, no, or default (use the server wide default). Disabling geo-filtering on a domain will disable all policies for that domain. There is a slight performance penalty with geo-filtering enabled (The geo-information has to be queried for every request) so you may only want to enable it on domains that require it.
Policy Examples
1. To only allow users from North America to login to your wordpress:
Location: /wp-login.php
Action: allow
Entity: continent
Content: North America2. To only allow users on the Rogers Communications Network (ASN 812) to login to your wordpress admin area:
Location: /wp-admin/.*
Action: allow
Entity: ASN
Content: 8123. To deny China from accessing your entire domain:
Location: .*
Action: deny
Entity: country
Content: ChinaTesting a Policy
AlmaLinux / CloudLinux / Rockylinux
First enable the mod_remoteip Apache module. Create the file /etc/httpd/conf.d/remoteip.conf with the following contents:
LoadModule remoteip_module modules/mod_remoteip.so
RemoteIPHeader X-Forwarded-ForRestart Apache
systemctl restart httpdDebian / Ubuntu
First enable the mod_remoteip Apache module:
a2enmod remoteipRestart Apache
systemctl restart apache2You can test a policy on the command line using curl with (replacing the <ipaddress> with one from a country that you blocked and <URL> with the URL that you created the policy for). Note: This command must be run on the same server that Juggernaut is installed on otherwise setting the X-Forwarded-For header will not work:
curl -k -I --header "X-Forwarded-For: <ipaddress>" "<URL>"Example (we created a policy for the domain to block Canada):
curl -k -I --header "X-Forwarded-For: 216.138.192.20" "https://www.example.com/"
HTTP/1.1 403 Forbidden
Server: nginx
Date: Tue, 27 Jul 2021 07:03:02 GMT
Content-Type: text/html
Content-Length: 1020
Connection: keep-alive
Last-Modified: Fri, 29 Aug 2014 13:20:26 GMT
ETag: "3fc-501c48428f649"
Accept-Ranges: bytesPHP Geolocation Information
After the mod_maxmind Apache module is loaded and geo-filtering is enabled then PHP has access to the geolocation information for any connecting IP address (MaxMind geo-information is stored in the $_SERVER array):
ASN_DB_NETWORK => 104.208.0.0/13
MM_ASORG => MICROSOFT-CORP-MSN-AS-BLOCK
MM_ASN => 8075
CITY_DB_NETWORK => 104.215.128.0/17
MM_COUNTRY_NAME => Singapore
MM_CONTINENT_NAME_EN => Asia
MM_COUNTRY_CODE => SG
MM_LATITUDE => 1.30360
MM_CONTINENT_CODE => AS
MM_LONGITUDE => 103.85540
MM_CITY_NAME => Singapore
MMDB_INFO => result found
MMDB_ADDR => 104.215.148.63Below is a PHP script that you can use to lookup the information for an IP address:
<?php
$maxmind = array(
'CITY_DB_NETWORK',
'MM_LATITUDE',
'MM_CONTINENT_CODE',
'MM_LONGITUDE',
'MM_CITY_NAME',
'MM_COUNTRY_NAME',
'MM_CONTINENT_NAME_EN',
'MM_COUNTRY_CODE',
'ASN_DB_NETWORK',
'MM_ASN',
'MM_ASORG',
'MMDB_INFO',
'MMDB_ADDR'
);
foreach ($_SERVER as $key => $value)
{
if (in_array($key, $maxmind))
{
echo $key .' => '. $value . PHP_EOL;
}
}
?>Save the script to one of your domains on your server as maxmind.php then call it on the command line:
curl -k --header "X-Forwarded-For: 104.215.148.63" "https://www.example.com/maxmind.php"
ASN_DB_NETWORK => 104.208.0.0/13
MM_ASORG => MICROSOFT-CORP-MSN-AS-BLOCK
MM_ASN => 8075
CITY_DB_NETWORK => 104.215.128.0/17
MM_COUNTRY_NAME => Singapore
MM_CONTINENT_NAME_EN => Asia
MM_COUNTRY_CODE => SG
MM_LATITUDE => 1.30360
MM_CONTINENT_CODE => AS
MM_LONGITUDE => 103.85540
MM_CITY_NAME => Singapore
MMDB_INFO => result found
MMDB_ADDR => 104.215.148.63Troubleshooting
Centos/RHEL/AlmaLinux
On Centos/RHEL/AlmaLinux the mod_maxmind module package name is mod_maxminddb.
To enable/disable the module in Apache:
Edit the file /etc/httpd/conf.d/maxminddb.conf and comment out the LoadModule line to disable the extension:
#LoadModule maxminddb_module modules/mod_maxminddb.so
<IfModule maxminddb_module>
MaxMindDBFile CITY_DB /usr/share/GeoIP/GeoLite2-City.mmdb
MaxMindDBEnv MM_CONTINENT_CODE CITY_DB/continent/code
MaxMindDBEnv MM_CONTINENT_NAME_EN CITY_DB/continent/names/en
MaxMindDBEnv MM_COUNTRY_CODE CITY_DB/country/iso_code
MaxMindDBEnv MM_COUNTRY_NAME CITY_DB/country/names/en
MaxMindDBEnv MM_CITY_NAME CITY_DB/city/names/en
MaxMindDBEnv MM_LONGITUDE CITY_DB/location/longitude
MaxMindDBEnv MM_LATITUDE CITY_DB/location/latitude
MaxMindDBNetworkEnv CITY_DB CITY_DB_NETWORK
MaxMindDBFile ASN_DB /usr/share/GeoIP/GeoLite2-ASN.mmdb
MaxMindDBEnv MM_ASN ASN_DB/autonomous_system_number
MaxMindDBEnv MM_ASORG ASN_DB/autonomous_system_organization
MaxMindDBNetworkEnv ASN_DB ASN_DB_NETWORK
</IfModule>Restart Apache:
systemctl restart httpdDebian/Ubuntu
On Debian/Ubuntu the mod_maxmind module package name is libapache2-mod-maxminddb.
To enable the module in Apache:
a2enmod maxminddbTo disable the module in Apache:
a2dismod maxminddbRestart Apache:
systemctl restart apache2
